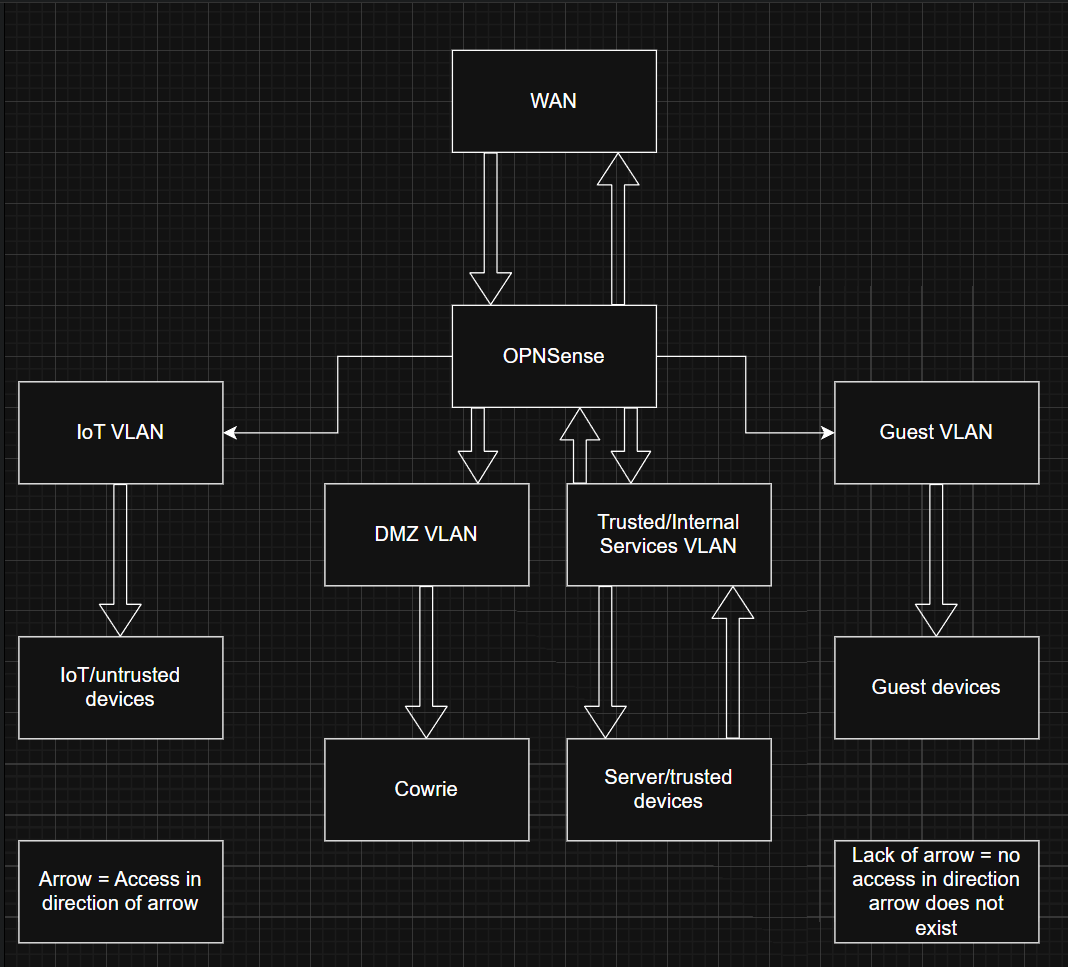
This site documents a self-hosted security lab designed to demonstrate network segmentation, detection engineering, and automated response.
This diagram shows trust boundaries, VLAN segmentation, and enforced access paths within the lab environment.
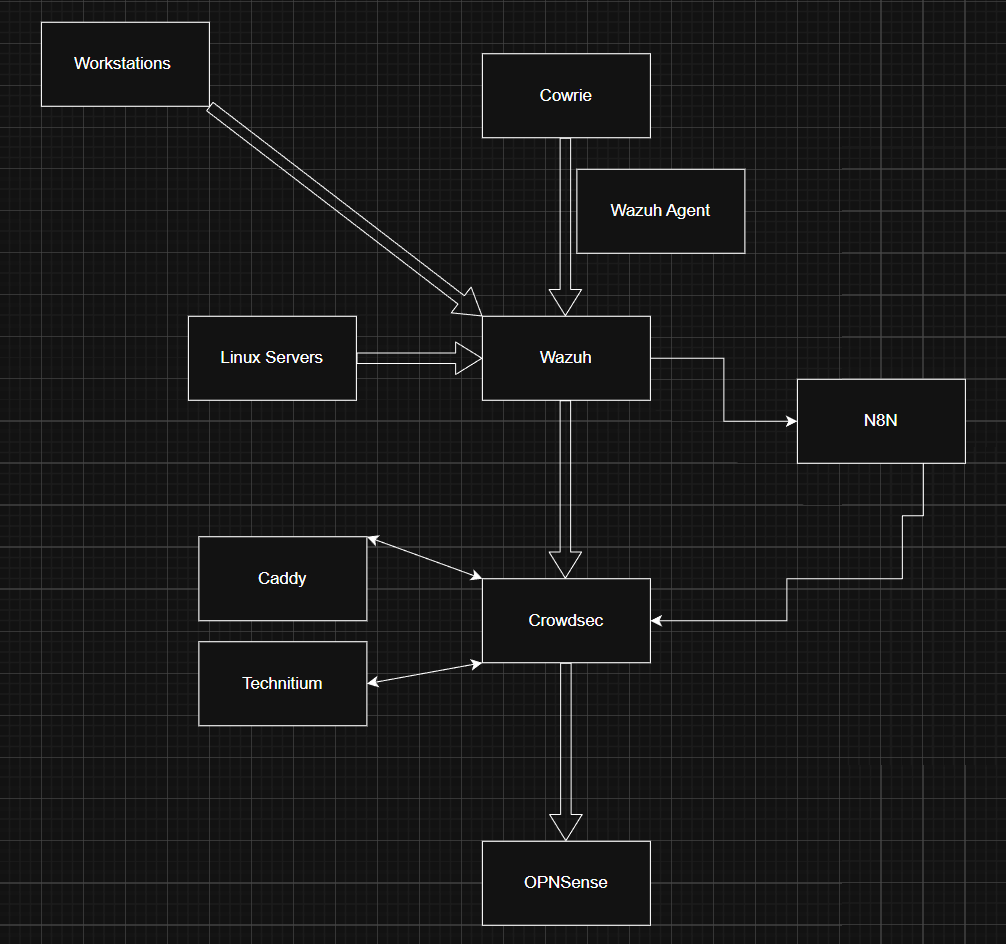
This diagram illustrates how telemetry flows from sensors through analysis, automation, and enforcement.
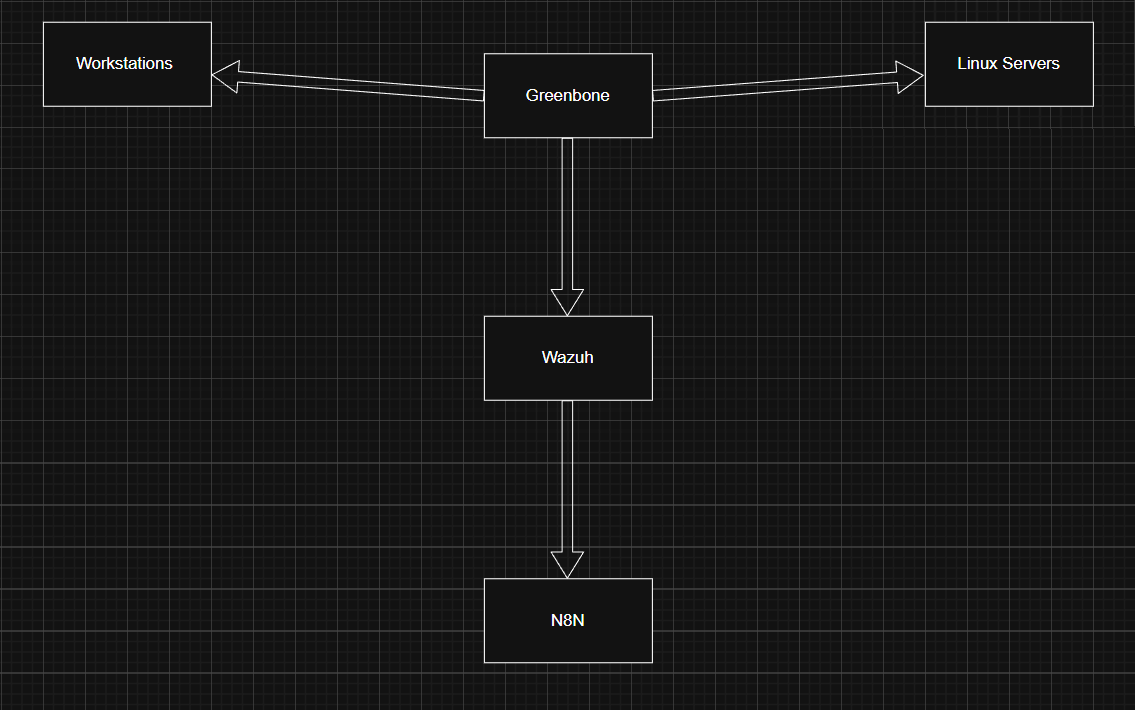
This diagram outlines how vulnerability scan results are correlated with system telemetry to identify exposed services, prioritize risk, and generate actionable security events.
The focus is on separating continuous vulnerability assessment from real-time detection, while still enabling automated alerting and response when high-risk conditions are identified.
Source code and documentation available upon request.